A symmetric cipher is one that uses the same key for encryption and decryption. Symmetric ciphers use symmetric algorithms to encrypt and decrypt data.
Traditional symmetric-key ciphers are not used today, but we study them for several reasons: First, they are simpler than modern ciphers and easier to understand. Second, they show the basic foundation of cryptography and encipherment: This foundation can be used to better understand modern ciphers.
Traditional ( Classical ) symmetric-key ciphers can be classified into two broad categories:
· Substitution Cipher
· Transposition Cipher
Substitution Cipher:
A substitution cipher replaces one symbol with another. Substitution Technique is a way of encrypting the message where characters or symbols replace the original plaintext. It is a classical encryption technique where the characters present in the original message are replaced by the other characters or numbers or by symbols. If the plain text (original message) is considered as the string of bits, then the substitution technique would replace bit pattern of plain text with the bit pattern of cipher text.
Substitution ciphers can be categorized as either Monoalphabetic ciphers and Polyalphabetic ciphers.
Monoalphabetic cipher is a substitution cipher, where the cipher alphabet for each plain text alphabet is fixed, for the entire encryption. In monoalphabetic substitution cipher, a character in a plaintext is always restored or changed to the similar character in the ciphertext indifferent of its position in the text.
In simple words, if the alphabet ‘p’ in the plain text is replaced by the cipher alphabet ‘d’. Then in the entire plain text wherever alphabet ‘p’ is used, it will be replaced by the alphabet ‘d’ to form the ciphertext.
For instance, if a letter A in the plaintext is changed to G then each appearance of A in the plaintext will be restored by G.
Plaintext : HELLO
Ciphertext : IFMMP
This is a monoalphabetic cipher as both L’s are encrypted as ‘M’.
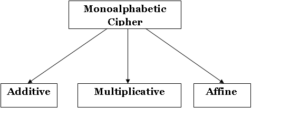
Types of monoalphabetic ciphers are:
Monoalphabetic Cipher:
Additive Cipher:
The simplest mono-alphabetic cipher is additive cipher. It is also referred to as ‘Shift Cipher’ or ‘Caesar Cipher’.
Encryption: C= (P+K) mod 26
Decryption: P=(C-K) mod 26
where,
C : Cipher-text
P : Plain-text
K : Key
Example:
Plaintext=HELLO, Key=3
Encryption:
C= (P+K) mod26
H-7, E-4, L-11, L-11, O-14
(7+3) mod26=10 mod 26=10 =K
(4+3) mod26= 7 mod 26 =7 =H
(11+3) mod26= 14 mod 26=14 =O
(11+3) mod 26= 14 mod 26=14= O
(14+3) mod 26= 17 mod 26= 17= R
Ciphertext= KHOOR
Decryption:
P= (C-K) mod26
Ciphertext= KHOOR, Key=3
K-10, H-7, O-14, O-14, R-17
(10-3) mod26=7 mod 26=7 =H
(7-3) mod26= 4 mod 26 =4 =E
(14-3) mod26= 11 mod 26=11 =L
(14-3) mod 26= 11 mod 26=11= L
(17-3) mod 26= 14 mod 26= 14= O
Plaintext= HELLO
Multiplicative Cipher:
The multiplicative cipher is similar to additive cipher except the fact that the key bit is multiplied to the plain-text symbol during encryption. Likewise, the cipher-text is multiplied by the multiplicative inverse of key for decryption to obtain back the plain-text.
Encryption: C=(P*K) mod 26
Decryption: P = (C * K-1) mod n
where,
K-1: multiplicative inverse of K (Key)
Affine Ciphers:
The affine cipher is a combination of additive cipher and multiplicative cipher.
Encryption:
C= (ax+b)mod26
Decryption:
P = a-1(x-b)mod26
Polyalphabetic Cipher:
Polyalphabetic cipher is more secure than monoalphabetic cipher. Monoalphabetic cipher maps one ciphertext with one plaintext. Comparatively, polyalphabetic cipher replaces plaintext with different ciphertext.
In polyalphabetic substitution, each appearance of a character in the plaintext can have a different substitution character in the ciphertext.
The relationship among a character in plaintext and a character in ciphertext is one to many. For instance, letter ‘A’ can be restored by the letter ‘C’ and the similar letter ‘A’ can be restored by ‘N’ later in the ciphertext.
In polyalphabetic cipher, frequencies of plaintext letter are not reflected in the ciphertext. Therefore, breaking of polyalphabetic cipher is complex than monoalphabetic cipher as statistical analysis cannot be used on it.
The main feature of polyalphabetic substitution cipher are the following:
· It is needed a set of associated monoalphabetic substitution rules.
· It need a key that decides which rule is used for which transformation.
· It can hiding the letter frequency of the underlying language including Playfair Cipher, Vigenere Cipher, and Hill Cipher.
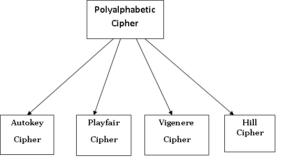
Autokey Cipher:
Encryption:
Ci= (Pi+Ki) mod 26
Decryption:
Pi=(Ci-Ki) mod 26
Playfair Cipher:
The playfair cipher is also known as Playfair Square. It is a cryptographic technique used for manual encryption of information. This scheme was developed by Charles Wheatstone in 1854.
The Playfair cipher was used by the British army in World War I and by the Australian in World War II. This was applicable because the playfair cipher is perfectly fast to use and does not demand some specific equipment to be used.
Playfair cipher is a substitution cipher which involves a 5X5 matrix.
Rules for generating ciphertext in Playfair Cipher:
- Firstly, create a 5×5 matrix from given keyword.
- Secondly, create pairs of alphabets, if same letters are there in pair, add ‘x’ in between.
- Thirdly, if pair appears in same row, shift the letter with immediate right letter.
- If pair appears in same column, replace it with the letter below it.
- In case pairs are in different rows and columns, replace it with the letters on corner of same row.
For instance, Keyword: OCCURENCE,
Plaintext: TALL TREES.
Here, resultant pair will be: TA LX LT RE ES.
Keyword matrix is as follows:
|
O |
C |
U |
R |
E |
|
N |
A |
B |
D |
F |
|
G |
H |
I/J |
K |
L |
|
M |
P |
Q |
S |
T |
|
V |
W |
X |
Y |
Z |
5×5 matrix in Playfair Cipher:
Hence, here ‘TA’ are in different rows and columns, so replace it by ‘PF’. Thus, ciphertext = PF IZ TZ EO RT
Vigenere Cipher:
Encryption: Ci= (Pi+Ki) mod 26
Decryption: Pi=(Ci-Ki) mod 26
Hill CIPHER:
Invented by Lester S. Hill in 1929, the Hill cipher is a polyalphabetic substitution cipher based on linear algebra. Hill cipher used matrices and matrix multiplication to mix up the plaintext.
Firstly, in hill cipher, we create a square matrix of key and we also form a matrix of plaintext. Secondly, the general equation is as follows:
Hence, for encryption, C =( P x K)mod26, here P = plaintext and K = Key.
Moreover, for decryption, P = (C x K-1 )mod26.
For instance, keyword = HILL and Plaintext = EXAM, we create a 2×2 matrix of HILL and 2×1 matrix of (EX) and (AM) respectively.
Similarly, for decryption we need to find inverse of K and then multiply it by cipher value. Lastly, we need to calculate mod 26.
Advantages of Hill Cipher:
· It is extremely effective in concealing single-letter frequencies
· For hiding both single-letter and two-letter frequency information, 3×3 hill ciphers are extremely efficient.
· Cipher provides great security against any kind of attack made through cipher text.
Transposition Cipher:
Transposition technique is an encryption method which is achieved by performing permutation over the plain text. Mapping plain text into cipher text using transposition technique is called transposition cipher.
The transposition technique is a cryptographic technique that converts the plain text to cipher text by performing permutations on the plain text, i.e., changing each character of plain text for each round. The substitution technique substitutes a plain text symbol with a cipher text symbol. On the other hand, the transposition technique executes permutation on the plain text to obtain the cipher text.
Transposition Techniques
1. Rail Fence Transposition
2. Columnar Transposition
3. Improved Columnar Transposition
Rail-Fence Technique:
Rail-Fence is the simplest transposition technique in which the plaintext is written down as a sequence of diagonals and then reading it row by row to produce the ciphertext.
For example, to encipher the message “meet me tomorrow” with a rail fence of depth 2, we write the following:
|
m |
|
e |
|
m |
|
t |
|
m |
|
r |
|
o |
|
|
|
e |
|
t |
|
e |
|
o |
|
o |
|
r |
|
w |
Once you have written the message as a sequence of diagonals, to obtain the cipher text out of it you have to read it as a sequence of rows. So, reading the first row the first half of cipher text will be:
m e m t m r o
reading the second row of the rail fence, we will get the second half of the cipher text:
e t e o o r w
Now, to obtain the complete cipher text combine both the halves of cipher text and the complete cipher text will be:
Cipher Text: M E M T M R O E T E O O R W
Rail fence cipher is easy to implement and even easy for a cryptanalyst to break this technique. So, there was a need for a more complex technique.
Columnar Transposition Technique
A. Basic Technique:
The columnar transposition cipher is more complex as compared to the rail fence. The steps to obtain cipher text using this technique are as follow:
Step 1: The plain text is written in the rectangular matrix of the initially defined size in a row by row pattern.
Step 2: To obtain the cipher text read the text written in a rectangular matrix column by column. But you have to permute the order of column before reading it column by column. The obtained message is the cipher text message.
B. Columnar Transposition Technique with Multiple Rounds
It is similar to the basic columnar technique but is introduced with an improvement. The basic columnar technique is performed over the plain text but more than once. The steps for columnar technique with multiple rounds are as follow:
Step 1: The plain text is written in the rectangle of predetermined size row by row.
Step 2: To obtain the cipher text, read the plain text in the rectangle, column by column. Before reading the text in rectangle column by column, permute the order of columns the same as in basic columnar technique.
Step 3: To obtain the final cipher text repeat the steps above multiple time.
Difference between Substitution Cipher Technique and Transposition Cipher Technique
Both Substitution cipher technique and Transposition cipher technique are the types of Traditional cipher which are used to convert the plain text into cipher text.
Substitution Cipher Technique:
In Substitution Cipher Technique plain text characters are replaced with other characters, numbers and symbols as well as in substitution Cipher Technique, character’s identity is changed while its position remains unchanged.
Transposition Cipher Technique:
Transposition Cipher Technique rearranges the position of the plain text’s characters. In transposition Cipher Technique, The position of the character is changed but character’s identity is not changed.
|
S.NO |
Substitution Cipher Technique |
Transposition Cipher Technique |
|
1. |
In substitution Cipher Technique, plain text characters are replaced with other characters, numbers and symbols. |
In transposition Cipher Technique, plain text characters are rearranged with respect to the position. |
|
2. |
Substitution Cipher’s forms are: Mono alphabetic substitution cipher and poly alphabetic substitution cipher. |
Transposition Cipher’s forms are: Key-less transposition cipher and keyed transposition cipher. |
|
3. |
In substitution Cipher Technique, character’s identity is changed while its position remains unchanged. |
While in transposition Cipher Technique, The position of the character is changed but character’s identity is not changed. |
|
4. |
In substitution Cipher Technique, the letter with low frequency can detect plain text. |
While in transposition Cipher Technique, the Keys which are nearer to correct key can disclose plain text. |
|
5. |
The example of substitution Cipher is Caesar Cipher. |
The example of transposition Cipher is Rail Fence Cipher. |
Difference between Monoalphabetic Cipher and Polyalphabetic Cipher:
|
SR.NO |
Monoalphabetic Cipher |
Polyalphabetic Cipher |
|
1 |
Monoalphabetic cipher is one where each symbol in plain text is mapped to a fixed symbol in cipher text. |
Polyalphabetic cipher is any cipher based on substitution, using multiple substitution alphabets. |
|
2 |
The relationship between a character in the plain text and the characters in the cipher text is one-to-one. |
The relationship between a character in the plain text and the characters in the cipher text is one-to-many. |
|
3 |
Each alphabetic character of plain text is mapped onto a unique alphabetic character of a cipher text. |
Each alphabetic character of plain text can be mapped onto ‘m’ alphabetic characters of a cipher text. |
|
4 |
It includes additive, multiplicative, affine and monoalphabetic substitution cipher. |
It includes autokey, Playfair, Vigenere, Hill, one-time pad, rotor, and Enigma cipher. |
|
5 |
It is a simple substitution cipher. |
It is multiple substitutions cipher. |
|
6 |
Monoalphabetic Cipher is described as a substitution cipher in which the same fixed mappings from plain text to cipher letters across the entire text are used. |
Polyalphabetic Cipher is described as substitution cipher in which plain text letters in different positions are enciphered using different cryptoalphabets. |
|
7 |
Monoalphabetic ciphers are not that strong as compared to polyalphabetic cipher. |
Polyalphabetic ciphers are much stronger. |