AES is an acronym for Advanced Encryption Standards. It is a cryptography standard that is used to encrypt and decrypt data to keep it secure. It is an encryption algorithm created by the National Institute of Science and Technology (NIST) in 2001.
AES is a symmetric key block cipher which means it uses the same key for both encryption and decryption. AES was first called Rijndael after its two developers, Belgian cryptographers Vincent Rijmen and Joan Daemen. AES offers far greater security than DES for communications and commercial transactions over the Internet.
There are some weaknesses in DES, so to overcome the weaknesses of DES, AES will be published. AES is widely used today as it is a much stronger than DES and triple DES despite being harder to implement. It encrypts data in blocks of 128 bits each. AES will operate on 128 bits of plaintext to produce 128 bits of ciphertext.
AES encryption is the most widely used standard around the world. This is one of the most common encryption standards used today, and it’s available in three key sizes: 128, 192, and 256 bits. Longer keys provide better security. The longer the key, the stronger the encryption. So, AES 128 encryption is the weakest, while AES 256 encryption is the strongest. In terms of performance though, shorter keys result in faster encryption times compared to longer keys. So 128 bit AES encryption is faster than AES 256 bit encryption.
The security of an AES system increases exponentially with key length. With even a 128-bit key, the task of cracking AES by checking each of the 2128 possible key values (a “brute force” attack) is so computationally intensive that even the fastest supercomputer would require, on average, more than 100 trillion years to do it. In fact, AES has never been cracked, and based on current technological trends, is expected to remain secure for years to come.
AES 256-bit encryption is the strongest and most robust encryption standard that is commercially available today. 256-bit encryption was not commonly used when the AES standards were first introduced in 2000, as using 256-bit encryption caused slower execution speeds in most networks given the higher processing demands. However, most devices today have much faster processors, and using 256-bit encryption does not typically slow down job execution significantly.
The Advanced Encryption System (AES) is the current encryption standard for most government and private sector IT security purposes. AES was chosen as the U.S. government security standard in 2001, and eventually also evolved into the encryption standard for most private sector enterprises.
A brief history of AES development:
In 1970, The National Bureau of Standards (NBS) in the United States needed a secret algorithm to encrypt critical government data. On this need, a new symmetric key algorithm: Data Encryption Standard (DES) has been revealed.
In 1997, The DES algorithm was discovered to be vulnerable to brute-force attacks. The National Institute of Standards and Technology (NIST) has launched a public competition to discover an alternative for the DES algorithm.
In 1998, 15 different groups from all over the world participated in the contest organized by NIST by submitting their own AES algorithms.
In 2001, The Rijndael group was chosen by NIST as the winner of the AES competition.
After all long-term selection and validation tests, The Advanced Encryption Standard (AES) was published as FIPS 197 on November 26, 2001.
Features of AES:
Following are the features of AES:
· AES algorithm works on the principle of Substitution-Permutation network.
· AES doesn’t use a Feistel network and is fast in both software and hardware.
· AES operates on a 4 x 4 matrix of bytes.
· The AES cipher is specified as a number of repetitions of transformation rounds that converts the input plaintext into the final output of cipher text.
· Each round consists of several processing steps.
· A set of reverse rounds are applied to transform cipher text back into the original plaintext using the same encryption key.
Benefits of Advanced Encryption Standard(Advantages of Advanced Encryption Standard) :
There are many reasons why AES is so popular, including:
· Robust Security:
AES 256 is the most secure encryption developed so far and is used by the United States federal government for even the most sensitive information. Because of its impracticality to crack, it is accepted worldwide as a reliable algorithm.
· Standardized Algorithm:
NIST has standardized the AES algorithm and made it an open-source resource, so it becomes easier for the general public to accept it as trustworthy. There are also no interoperability issues as hardware, software, and firmware all use the same algorithm.
· Variable Key Lengths:
AES encryption can be done using different key lengths, including 128-bit, 192-bit, and 256-bit keys. For a businessperson using AES to protect their eCommerce account, 128-bit is ideal. Governments protecting their sensitive documents can use AES-256 for greater security.
· Fast Encryption/Decryption Speed:
The processing speed of AES encryption is faster than both DES and Triple-DES. On the same hardware, AES is around six times faster than Triple-DES.
Where Is AES Used?
AES is the most widely trusted encryption standard in the world. The AES algorithm is widely used in a variety of applications, including wireless security, processor security, file encryption, and SSL/TLS. AES encryption is used regularly by federal government departments as well as non-government entities, commercial firms, and organizations, to secure sensitive data.
AES encryption is now used in devices and applications that are also used by consumers today. For example, SSDs for data storage, Google Cloud storage service, internet browser programs such as Firefox and Opera, security certificates for websites. Many popular apps (such as Snapchat and Facebook Messenger) use AES encryption to safely send information such as photographs and messages.
Well-known file compression programs such as 7z, WinRAR, Winzip also use the AES algorithm to prevent data breaches. AES encryption is also implemented in the libraries of programming languages such as Java, Python, and C++.
Why was AES developed?
The main usage purpose of the Advanced Encryption Standard (AES) is to encrypt data and protect it from unauthorized access. This is accomplished through the use of a cryptographic process key of various lengths. Depending on the length, this is labeled AES-128, AES-192, or AES-256.
The Advanced Encryption Standard was created as a replacement for the Data Encryption Standard, or DES. DES was found to be increasingly more vulnerable to brute-force attackers, and thus needed to be phased out. AES’ original creation was to protect sensitive government information, but the security and ease of implementation provided by AES caused the majority of organizations to utilize AES in their encryption processes. Both public and private sector companies use AES now, as it protects against cyber-attacks, like brute force. AES does present an issue when exporting products encrypted with this encryption algorithm.
Why is Advanced Encryption Standard (AES) Used?
The AES encryption method is widely renowned for its speed and security. The security of the algorithm comes from the data being encrypted using a complex block cipher technique. And AES uses less processing power so it is faster than other equivalents.
Being the Advanced Encryption Standard (AES), a key standard for cryptography is in the process of data encryption and privacy. It acts as the most popular cipher and used for a wide range of applications comprising even the US Government use AES for ensuring data privacy and security. Advanced Encryption Standard(AES) is symmetrical and stands away from the stream cipher where each character is encrypted one at the moment. Symmetric means the same kind of keys is used in the encryption process. It is also very robust for hackers because of its large key sizes. The key sizes used here are very higher as like 128, 192 and 256 bits for encryption. Commercially his cipher protocol is among the most widely used ones all around the world.
Attacks on AES:
Researchers continually attempt to break AES with methods that are viable. The reason researchers are attempting to crack AES is to be one step ahead of attackers. If an attacker were to crack AES, and keep it a secret, then the world would continue to use AES believing it is completely secure. So far, a few different, theoretical attacks have been proposed, including:
· Related-key attack: A related-key attack involves identifying how a cipher works under different keys. This cryptanalysis technique involves feeding a cipher, used to encrypt data, several different keys with the same plaintext. The process that occurs between the key and cipher can help identify a mathematical relationship between the cipher and key, thus helping identify the actual key’s value. This attack method is, however, not considered a big threat to AES, as it is useless as long as the protocols were implemented correctly.
· Distinguished key attack: An attack that used a known key to find out the inner workings of an 8 round AES-128 algorithm was successfully used. As this was done on an 8 round algorithm, as opposed to the official 10 round algorithm, this is an attack that should not cause issues with any official AES algorithms.
· Side channel attack: A side channel attack involves the leaking of information from an organization’s infrastructure. The data is leaked through locations, and the attacker listens at in to the sound, timing information, electromagnetic information or the power consumption in order to gather inferences from the algorithm which can then be used to break it. This can be stopped, however, by fixing the source of the leak or ensuring no pattern exists in the leaking information.
· Key compromise: Though not a direct attack on the AES algorithm, the compromise of the key used for encryption cripples the entire AES algorithm. This is why proper key management and security are vital to the IT infrastructure of any organization.
· Quantum computing: Quantum computing is the successor to classical computing, which we do now, that is still in the process of being created and understood. Though it has not been fully realized yet, the creation of quantum computers will make all classical computing cryptography irrelevant, as quantum computing could crack any classical cryptography algorithm in potentially seconds.
Working of AES (How Does AES Encryption Work?)
Unlike its predecessor DES, AES does not use a Feistel network. It works on a substitution permutation network where a series of different operations are linked together.
AES encryption takes the plaintext input data and divides it into 128-bit chunks of data called blocks. Each block is 128 bits long, so each time 128 bits of plaintext is submitted to the program, 128 bits of ciphertext is generated.
A single cryptographic key is then used to generate different subkeys — sometimes called round keys because a separate subkey is used for each round of processing -that will be applied to the different chunks of data. This produces a ciphertext for that data block. It’s also important to note that no two round keys are similar.
Each block of ciphertext is then added onto the next until, finally, the final ciphertext is created that is the same size as the initial input data.
Depending on the size of the key used, the data will go through 10, 12 or 14 rounds of processing. A 128-bit key requires 10 rounds while a 192-bit key requires 12 rounds. A full 14 rounds are required when a 256-bit key is being used. The longer the key, the more secure the encryption.
AES Structure: (General structure)
AES encryption takes a plaintext block size of 128 bits, or 16 bytes. The key length can be 16, 24 0r 32 bytes (128,192 or 256 bits). The algorithm is referred to as AES-128, AES-192, or AES-256, depending on the key length.
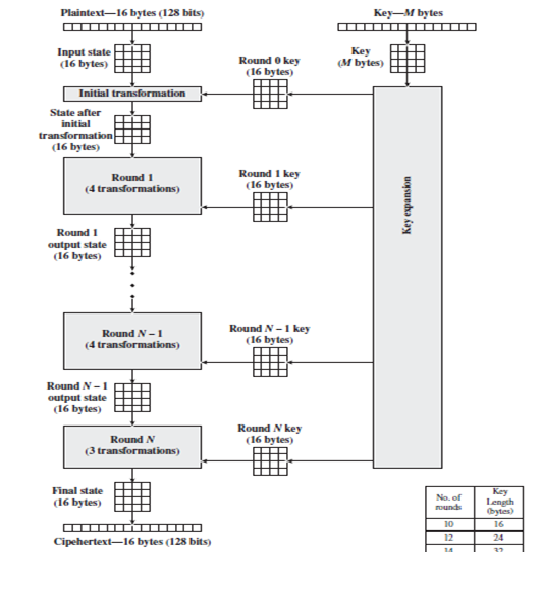
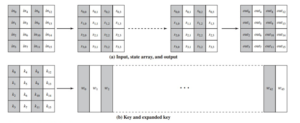
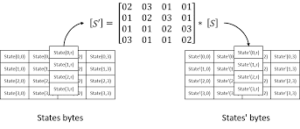
The input to the encryption and decryption algorithms is a single 128-bit block. This block is depicted as a 4 X 4 square matrix of bytes. This block is copied into the State array, which is modified at each stage of encryption or decryption. After the final stage, State is copied to an output matrix. These operations are depicted in figure-(a) below. Similarly the key is depicted as a square matrix of bytes. This key is then expanded into an array of key schedule words. Figure-(b) shows the expansion for the 128-bit key. Each word is four bytes, and the total key schedule is 44 words for the 128-bit key. The ordering of bytes within a matrix is by column. So, for example, the first four bytes of a 128-bit plaintext input to the encryption cipher occupy the first column of the in matrix, the second four bytes occupy the second column, and so on. Similarly, the first four bytes of the expanded key, which form a word, occupy the first column of the w matrix.
The cipher consists of N rounds, where the number of rounds depends on the key length: 10 rounds for a 16-byte key, 12 rounds for a 24-byte key, and 14 rounds for a 32-byte key. The first N-1 rounds consist of four distinct transformation functions: SubBytes, shiftRows, MixColumns, and AddRoundKey. The final round contains only three transformations, and there is a initial transformation (AddRoundKey) before the first round, which can be considered round 0. Each transformation takes one or more 4 x 4 matrices as input and produces a 4x 4 matrix as output. Figure below shows that the output of each is a 4×4 matrix, with the output of the final roundbeing the ciphertext. Also, the key expansion function generates N+1 round keys, each odf which is a distinct 4×4 matrix. Each round key serves as one of the inputs to the AddRoundKey transformation in each round.
Overall structure of AES Encryption process shown in figure below:
Figure: AES Encryption Process
Figure: AES Data Structure
AES Structure: (Detailed structure)
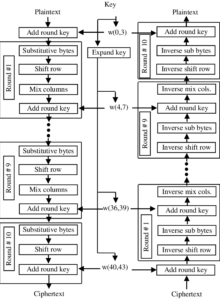
Figure below shows the AES cipher in more detail, indicating the sequence of transformations in each round and showing the corresponding decryption function. In the figure, we show encryption proceeding down the page and decryption proceeding up the page.
The no. of rounds are 10, key length is 128 bit. AES considers each block as a 16-byte (4 byte X 4 byte). For encryption, each round consists of the following four steps:
1. Substitute Bytes
2. Shift Rows
3. Mix columns
4. Add round keys
The last round doesn’t have the Mix Columns steps. The SubBytes does the substitution and ShiftRows and MixColumns performs the permutation in the algorithm. A subBytes transformation is done through S-Box.
Substitute Bytes (SubBytes):
This step implements the substitution. In this step each bytes is substituted by another byte. It is performed using a substitution table ( S-Box).
Here 16 input bytes are substituted by by looking up the S-Box table. The result is in a matrix of four rows and four columns. The SubBytes operation, which stands for substitute bytes, will take the 16-byte block and run it through an S-Box (substitution box) to produce an alternate value.
Shift Rows:
In the shift row step, each row r of the input (state) matrix is circularly shifted by r positions to the left, with the goal of permuting bytes between columns.
Each row is shifted a particular number of times. The shifting numbers are depended on the number of the row. Shift is carried out as follows:
· The first row is not shifted
· The second row is shifted once to the left.
· The third row is shifted twice to the left
· The fourth row is shifted thrice to the left.
Mix Columns:
MixColumns transformation, operates on each column individually. Each byte of a column is mapped into a new value that is a function of all four bytes in that column.The transformation can be defined by the following matrix multiplication on State.
Each element in the product matrix is the sum of products of elements of one row and one column.In this case, the individual additions and multiplications are performed in GF (28).
AddRound Key:
AddRoundKey is only a simple logical XOR of the state using a round key which is produced by the key expansion operation.
AES Key Expansion:
Key Expansion Algorithm:
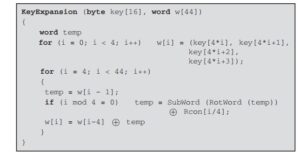
The AES key expansion algorithm takes as input a four-word (16-byte) key and produces a linear array of 44 words (176 bytes). This is sufficient to provide a four-word round key for the initial AddRoundKey stage and each of the 10 rounds of the cipher. The pseudocode below describes the expansion.
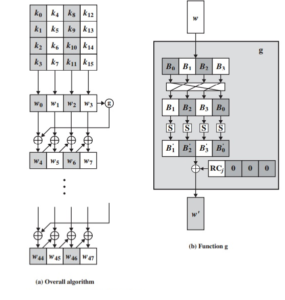
The key is copied into the first four words of the expanded key. The remainder of the expanded key is filled in four words at a time. Each added word w[i] depends on the immediately preceding word, w[i – 1], and the word four positions back, w[i – 4]. In three out of four cases, a simple XOR is used. For a word whose position in the w array is a multiple of 4, a more complex function is used. Figure below illustrates the generation of the expanded key, using the symbol g to represent that complex function.
The function g consists of the following subfunctions:
1. RotWord performs a one-byte circular left shift on a word. This means that an input word [B0, B1, B2, B3] is transformed into [B1, B2, B3, B0].
2. SubWord performs a byte substitution on each byte of its input word, using the S-box (Table 5.2a).
3. The result of steps 1 and 2 is XORed with a round constant, Rcon[j].
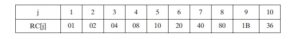
The round constant is a word in which the three rightmost bytes are always 0. Thus, the effect of an XOR of a word with Rcon is to only perform an XOR on the left- most byte of the word. The round constant is different for each round and is defined as Rcon[j] = (RC[j], 0, 0, 0), with RC[1] = 1, RC[j] = 2 RC[j –1] and with multiplica- tion defined over the field GF(28). The values of RC[j] in hexadecimal are: