Symmetric encryption ciphers consist of two main categories: block ciphers and stream ciphers. Block and stream ciphers are two ways that you can encrypt data.
Block cipher is an encryption and decryption method which operates on the blocks of plain text. A block cipher takes a fixed-length block of text say b bits and a key as input and produces a b-bit block of ciphertext. If the amount of plaintext to be encrypted is larger than b bits, it can be divided further.
For different applications and uses, there are several modes of operations for a block cipher. The different modes result in different properties being achieved which add to the security of the underlying block cipher. A mode of operation is a technique for enhancing the effect of a cryptographic algorithm.
When multiple blocks of plaintext are encrypted using the same key, a number of security issues arise. To apply a block cipher in variety of applications, five modes of operation have been defined by NIST.
1. Electronic Codebook (ECB)
2. Cipher Block Chaining (CBC)
3. Cipher Feedback (CFB)
4. Output Feedback (OFB)
5. Counter (CTR)
The five modes are intended to cover a wide variety of applications of encryption for which a block cipher could be used. These modes are intended for use with any symmetric block cipher, including triple DES and AES.
Electronic Code Book (ECB):
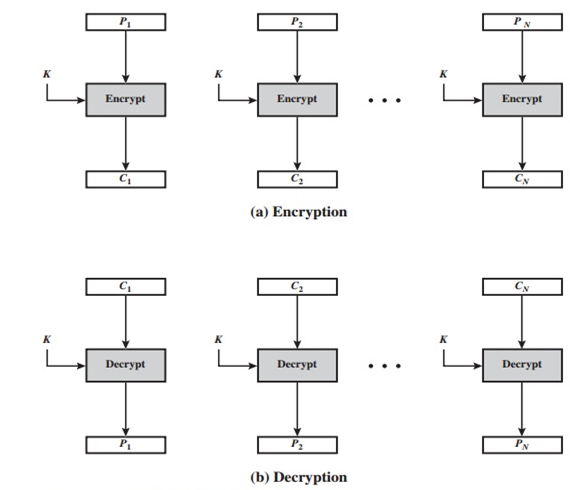
Electronic Codebook is the simplest block cipher mode. It is the most basic mode of operation for enhancing block ciphers. In Electronic Codebook mode, plaintext is encrypted using the same key. It is simpler because of direct encryption of each block of plaintext and output is in form of blocks of encrypted ciphertext. Generally, if a message is larger than b bits in size, it can be broken down into a bunch of blocks and the procedure is repeated.
For a message longer than b bits, the procedure is simply to break the message into b-bit blocks, padding the last block if necessary. Decryption is performed one block at a time, always using the same key.
In Figure above, the plaintext (padded as necessary) consists of a sequence of b-bit blocks, P1, P2, ……., PN. The corresponding sequence of ciphertext blocks is C1, C2, ……… , CN.
The ECB method is ideal for a short amount of data, such as an encryption key. Thus, if you want to transmit a DES or AES key securely, ECB is the appropriate mode to use.
The most significant characteristic of ECB is that if the same b-bit block of plaintext appears more than once in the message, it always produces the same ciphertext. For lengthy messages, the ECB mode may not be secure. If the message is highly structured, it may be possible for a cryptanalyst to exploit these regularities. For example, if it is known that the message always starts out with certain predefined fields, then the cryptanalyst may have a number of known plaintext-ciphertext pairs to work with. If the message has repetitive elements with a period of repetition a multiple of b bits, then these elements can be identified by the analyst. This may help in the analysis or may provide an opportunity for substituting or rearranging blocks.
Cipher Block Chaining (CBC):
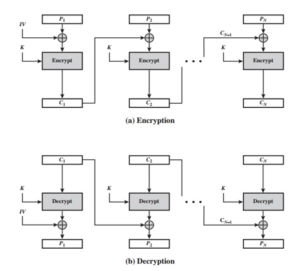
To overcome the security deficiencies of ECB, we would like a technique in which the same plaintext block, if repeated, produces different ciphertext blocks. A simple way to satisfy this requirement is the cipher block chaining (CBC) mode.
Cipher block chaining mode (CBC) produces different ciphertext blocks even with the same plaintext. This is because, the input to the encryption algorithm is the XOR of the current plaintext block and the previous ciphertext block. Also, an initialization vector, or IV, is used to XOR the first block of plaintext.
For decryption, each ciphertext block is passed through the decryption algorithm. The result is XORed with the previous ciphertext block to produce the plaintext block.
In CBC, the previous cipher block is given as input to the next encryption algorithm after XOR with the original plaintext block. To produce the first block of ciphertext, an initialization vector (IV) is XORed with the first block of plaintext. On decryption, the IV is XORed with the output of the decryption algorithm to recover the first block of plaintext. The IV is a data block that is the same size as the cipher block. The IV must be known to both the sender and receiver but be unpredictable by a third party.
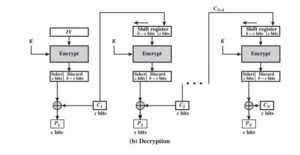
Cipher Feedback Mode (CFB):
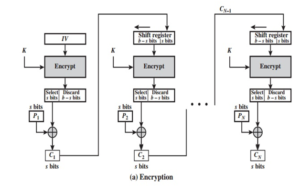
In this mode the cipher is given as feedback to the next block of encryption with some new specifications: first, an initial vector IV is used for first encryption and output bits are divided as a set of s and b-s bits. The left-hand side s bits are selected along with plaintext bits to which an XOR operation is applied. The result is given as input to a shift register having b-s bits to lhs,s bits to rhs and the process continues.
The input to the encryption function is a b-bit shift register that is initially set to some initialization vector (IV). The leftmost (most significant) s bits of the output of the encryption function are XORed with the first segment of plaintext P1 to produce the first unit of ciphertext C1, which is then transmitted. In addition, the contents of the shift register are shifted left by s bits, and C1 is placed in the rightmost (least significant) s bits of the shift register. This process continues until all polaintext units have been encrypted.
For decryption, the same scheme is used, except that the received ciphertext unit is XORed with the output of the encryption function to produce the plaintext unit. Note that it is the encryption function that is used, not the decryption function.
Output Feedback Mode (OFB):
The output feedback (OFB) mode is similar in structure to that of CFB. For OFB, the output of the encryption function is fed back to become the input for encrypting the next block of plaintext. In CFB, the output of the XOR unit is fed back to become input for encrypting next block.
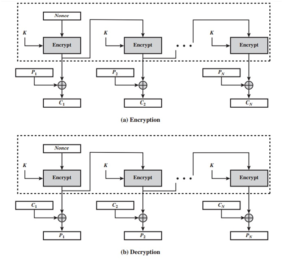
The other difference is that the OFB mode operates on full blocks of plaintext and ciphertext, whereas CFB operates on an s-bit subset. As with CBC and CFB, the OFB mode requires an initialization vector. In the case of OFB, the IV must be a nonce; that is, the IV must be unique to each execution of the encryption operation. The reason for this is that the sequence of encryption output bloc-ks, Oi, depends only on the key and the IV and does not depend on the plaintext.
Counter Mode (CTR):
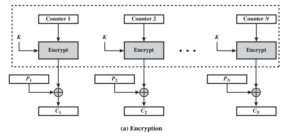
The Counter Mode or CTR is a simple counter-based block cipher implementation. Every time a counter-initiated value is encrypted and given as input to XOR with plaintext which results in ciphertext block.
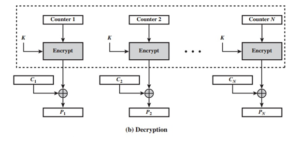
A counter equal to the plaintext block size is used. The only requirement is that the counter value must be different for each plaintext block that is encrypted. Typically, the counter is initialized to some value and then incremented by 1 for each subsequent block. For encryption, the counter is encrypted and then XORed with the plaintext block to produce the ciphertext block; there is no chaining. For decryption, the same sequence of counter values is used, with each encrypted counter XORed with a ciphertext block to recover the corresponding plaintext block. Thus, the initial counter value must be made available for decryption.