What is Computer Network?
A computer network is a group of two or more computers that are linked together. The primary purpose of a computer network is to enable the exchange of data and resources among connected devices.
The term computer network means an interconnected collection of autonomous computers. Two computers are said to be interconnected if they are able to exchange information. Computers are connected together so that they can share data, application and hardware devices.
The connection between computers can be established using a copper wire, lasers, microwaves and communication satellites. Any individual computer connected to a network is a workstation, and any individual device such as workstation, printer, scanner etc., connected to a network is called node. A workstation can be with or without hard disk drive.
The main utility of computer networks is involved in sharing resources between users. For instance, a co-worker on a floor can share a spreadsheet created by a worker on another floor, with none leaving his desk. Networks offer efficient communication among the employees through e-mail. Networks let them share software and peripherals like printers and scanners. With networking, an office can work with just one printer and one scanner for even ten workstations, thus networking helps save on equipment. A network may connect few computers in a room, or it may connect computers in different cities or even different countries.
Types of Computer Network: LAN MAN WAN
Computer networks are categorized based on their geographical scope and purpose. The choice of the type of network depends on factors such as the organization’s geographical spread, communication requirements, and the scale of the network needed to meet business objectives. In many cases, organizations use a combination of LANs, MANs, and WANs to create a comprehensive network infrastructure that meets their specific needs.
LAN (Local Area Network):
A LAN is a group of computers or other devices that are connected within a limited or small geographical area such as home, school, computer laboratory, office building or group of buildings. A LAN is composed of inter-connected computers and devices which are capable of accessing and sharing data and devices, such as printers, scanners and data storage devices, anywhere on the LAN. LANs provide a cost-effective and efficient way for devices within a limited area to communicate and share resources.
Scope: LANs covers a small geographic area, ranging from 10 meters to around 1000 meters (or 1 kilometre), such as a home, office or a building. The actual coverage of a LAN can vary depending on the specific technology and infrastructure used.
Purpose: LANs are designed for high-speed data transfer and are commonly used for connecting computers, devices, and resources within a limited area. LANs are ideal for local connectivity within a confined area and are characterized by high data transfer rates.
Technologies: Ethernet and Wi-Fi are the two most common technologies used for local area networks. Ethernet, for example, uses physical cables to connect devices, while Wi-Fi relies on wireless communication
Examples: Home networks, office networks, and university campus networks are common examples of LANs.
Advantages of LAN:
Resource Sharing: LANs allow for the sharing of resources such as files, printers, and internet access among connected devices. Therefore, there is no need to purchase separate resources for each computer, and it saves money.
High Data Transfer Rates: LANs provide high-speed data transfer rates, enabling fast communication between devices. This is essential for applications that require real-time data exchange, such as video conferencing or collaborative work.
Cost-Effective: LANs are cost-effective for connecting devices within a limited area. The infrastructure required for LANs, such as Ethernet cables and switches, is generally more affordable compared to wide-area networking technologies.
Improved Collaboration: LANs facilitate collaboration among users by enabling the easy sharing of files and resources. Collaborative tools, such as shared folders and networked applications, benefit from the local nature of the network.
Scalability: LANs are scalable, allowing organizations to expand their network easily by adding more devices or upgrading network equipment. This scalability is important for growing businesses or institutions.
Efficient Communication: LANs use dedicated network devices like switches, which provide efficient and direct communication between devices. This reduces network congestion and enhances overall network performance.
Security: LANs offer a level of inherent security since access to the network is limited to devices within the local area. Additional security measures, such as firewalls and access controls, can be implemented to enhance data protection.
Ease of Management: Managing a LAN is typically more straightforward compared to larger networks. IT administrators have greater control over network resources and can implement changes or updates with relative ease.
Disadvantages of LAN:
Limited Range: LANs are designed for a limited geographic area, typically within a single building or a campus. This limitation can be a drawback when trying to connect devices over a larger area.
High Initial Setup Costs: Setting up a LAN can involve significant upfront costs. This includes the cost of network hardware (routers, switches, cables), software licenses, and skilled personnel to design and implement the network.
Security Concerns: LANs are vulnerable to security threats, including unauthorized access, data interception, and malware attacks. Implementing and maintaining robust security measures is crucial to protect sensitive information.
Dependence on a Centralized Server: In client-server LAN architectures, the network relies on a centralized server. If any file on the server is corrupted or hard drive fails then all the attached computers face problems in functioning properly.
Limited Scalability: Expanding a LAN to accommodate a growing number of devices may require significant upgrades and reconfiguration. Scaling up a LAN can be more complex and costly as the network grows.
MAN (Metropolitan Area Network):
A Metropolitan Area Network (MAN) is a type of network that covers a larger geographical area than a Local Area Network (LAN) but is smaller than a Wide Area Network (WAN). MAN, typically covers a metropolitan area, which could be a single large city, multiple cities and towns or a large university campus.
Scope: The scope of MAN lies between LAN and WAN. MAN covers a larger geographical area than LAN but is smaller than WAN. The size usually ranges from 5 kilometres to 50 km.
Purpose: The purpose of a Metropolitan Area Network is to connect various local networks within a city or a metropolitan area. It facilitates high-speed data transfer and communication between different organizations, businesses, or institutions within the defined geographical region. MANs are often used to interconnect multiple buildings, campuses, or data centers within a city, providing efficient and reliable communication services.
Technologies: The technology used for MANs can vary, including fiber optic cables, wireless connections, and other high-speed networking technologies, depending on the specific requirements of the network and the available infrastructure in the area.
Examples: Municipal area networks, university networks spanning multiple campuses within a city, and corporate networks connecting multiple office locations are examples of MANs.
Advantages of MAN:
Geographic Coverage: MANs cover a larger geographic area compared to LANs. They can span across a city or a large campus, providing connectivity to multiple locations.
Scalability: MANs are designed to be scalable, allowing for the easy addition of new nodes or the expansion of the network to accommodate growing demands.
High Data Transfer Rates: MANs often offer higher data transfer rates compared to WANs (Wide Area Networks). This allows for faster communication and data exchange within the metropolitan area.
Interconnectivity: MANs provide a means to interconnect various LANs within a metropolitan area. This facilitates seamless communication and resource sharing between different locations.
Reliability: MANs are often designed with redundancy and failover mechanisms, improving network reliability. Redundant paths and backup connections help minimize downtime in case of a network component failure.
Disadvantages of MAN:
Cost of Implementation: Setting up a MAN can involve substantial initial costs. This includes the purchase of networking equipment, installation of infrastructure, and the hiring of skilled personnel for design and implementation.
Complexity of Management: MANs can become complex as they grow, making management and maintenance more challenging. Coordinating multiple interconnected networks and ensuring their optimal performance may require advanced network management skills.
Limited Coverage: While MANs cover alarger area than LAN, they may not provide sufficient coverage for extremely extensive geographical regions. In such cases, Wide Area Networks (WAN) might be more suitable.
Scalability Challenges: Expanding or scaling a MANcan be challenging. As the network grows, additional resources and infrastructure may be needed to maintain performance and accommodate increased traffic.
Security Concerns: MANs, like any network, are susceptible to security threats such as unauthorized access, data interception, and malware attacks. Ensuring robust security measures is crucial to protect sensitive information transmitted over the network.
WAN (Wide Area Network):
A Wide Area Network (WAN) is a type of network that covers a large geographic area. A WAN connects multiple Local Area Networks (LANs) or Metropolitan Area Networks (MANs) together. WANs are designed to facilitate communication and data exchange over long distances, often across cities, countries, continents, or even a global scale
Scope: WANs cover vast geographical areas and can connect devices and networks that are located far apart. They provide the infrastructure for long-distance communication.
Purpose: WANs are commonly used to connect multiple Local Area Networks (LANs) across a wide geographic area, providing communication and data exchange between different locations. They provide a means for organizations to connect their remote offices or branch locations. WANs are designed for long-distance communication and can connect LANs and MANs across vast distances.
Technologies: WANs employ a variety of technologies to transmit data over long distances, including dedicated leased lines, satellite links, microwave links, and technologies like MPLS (Multiprotocol Label Switching) and VPNs (Virtual Private Networks).
Examples: The Internet is a global WAN. Corporate networks that connect offices across different cities or countries also form WANs.
Advantages of WAN:
Geographic Coverage: WANs connect devices over vast geographical areas, making them suitable for linking offices, branches, and data centers located in different cities, countries, or continents.
Global Connectivity: WANs facilitate global connectivity, enabling organizations to connect and communicate with remote offices, partners, and clients worldwide. This is essential for multinational companies and businesses with a global presence.
Resource Sharing: WANs allow for efficient sharing of resources, including files, applications, and databases, across different locations. This improves collaboration and efficiency among users in various geographical areas.
Cost Efficiency: By centralizing certain services and resources, WANs can contribute to cost savings. For example, organizations can share expensive resources like servers or data storage across different locations.
Scalability: WANs are scalable and can accommodate the growing needs of an organizations. As the business expands, additional sites and users can be easily incorporated into the network.
Centralized Data Management: WANs support centralized data management, allowing organizations to maintain a single, centralized repository for data storage and backup. This simplifies data management and ensures data consistency across the network.
Improved Communications: WANs support effective communication through various services like email, video conferencing and instant messaging. This enhances real-time collaboration among users regardless of their physical location.
Disadvantages of WAN:
High Initial Setup Costs: Establishing a WAN involves significant costs. This includes the purchase of networking equipment, communication links, and the implementation of security measures. The initial investment can be substantial, especially for organizations with multiple remote locations.
Complexity of Implementation: WANs are more complex to design and implement than smaller networks. Organizations need skilled IT personnel to plan, configure, and manage the network, adding to the overall complexity and cost.
Maintenance Costs: WANs require ongoing maintenance and management. Regular monitoring, troubleshooting, and software updates are necessary to ensure optimal performance and address potential issues. Maintenance costs can accumulate over time.
Security Concerns: WANs are more susceptible to security threats such as data interception, unauthorized access, and cyberattacks. Implementing robust security measures, such as encryptions and firewalls, is essential to protect data during transmission.
Latency Issues: Due to the longer distances and multiple interconnected devices, WANs may experience latency or delays in data transmission. This can impact the performance of real-time applications, such as video conferencing and online gaming.
Complex Troubleshooting: Identifying and resolving issues in a WAN can be more complex than in a LAN. The distributed nature of the network makes troubleshooting challenging, and diagnosing problems may require specialized knowledge and tools.
Wired and Wireless Networks:
Wired and wireless networks are two common types of network configurations used to connect devices and enable communication. Each has its own set of advantages and disadvantages, and the choice between them depends on factors such as performance requirements, mobility, and the specific needs of the users.
Wired Networks:
The term “wired” refers to any physical medium made up of wires (cables). Wired networks use physical cables or wires to connect devices and transmit data. Common types of wired connections include twisted pair cables, fiber-optic cables, and coaxial cables.
Advantages:
- Reliability: Wired connections are generally more reliable than wireless connections. They are less susceptible to interference and are not affected by factors like signal strength or obstacles.
- Speed: Wired networks often provide higher data transfer rates, making them suitable for demanding applications such as large file transfers and streaming.
- Security: Wired networks are considered more secure because the physical connection is harder to intercept compared to wireless signals. It’s generally more challenging for unauthorized users to gain access to a wired network.
Disadvantages:
- Inflexibility: Devices in a wired network are physically connected, limiting flexibility.
- Installation and Maintenance: Setting up and maintaining wired infrastructure may require more effort and cost, especially in existing buildings.
- Limited Mobility: Devices need to be physically connected to the network, restricting movement compared to wireless networks.
Common Technologies:
- Ethernet is a common technology for wired networks, and it comes in various speeds such as 1 Gigabit Ethernet (1 GbE), 10 Gigabit Ethernet (10 GbE), etc.
- Fiber optics are used for high-speed and long-distance wired connections.
Wired Network Medium:
Wired network use three types of cable: twisted-pair, coaxial and fiber optic cable.
Twisted Pair:
Twisted pair consists of pairs of insulated copper wires twisted together and enclosed in a protective outer sheath. Twisting helps reduce electromagnetic interference from external sources and crosstalk between adjacent pairs, improving signal transmission.
There are two types of twisted-pair cables: UTP (unshielded twisted pair) and STP (shielded twisted pair). The main difference between both is STP uses an extra layer of coating on each pair. The additional layer of coating on each pair improves cable performance but increases the cost.
Unshielded Twisted Pair (UTP): It does not shield each pair individually. It uses only an outer cover to keep all pairs together. Since it uses only outer coating, it is much cheaper than STP. Due to low cost, flexibility, and good performance, it is mainly used in LAN networks. Almost all modern LAN networks use it to connect devices to the network. It can carry signals up to 100 meters. It is available in various grades or categories based on data transmission speed.
Shielded Twisted Pair (STP): The outer insulated jacket protects the twisted-pair cable only from physical stress or damage. However, it does not protect the cable from electromagnetic interference (EMI). If the network premise contains many electrical appliances, UTP cables do not work. In such a situation, instead of UTP, STP cables are used to connect devices. STP cables are expensive but includes additional shielding to reduce electromagnetic interference, providing better performance in environments with high interference.
Advantages:
- Cost-effective and widely available.
- Suitable for short to medium-distance communications.
- Easy to install and terminate.
Disadvantages:
- Limited bandwidth compared to other media.
- Susceptible to electromagnetic interference.
Coaxial Cable:
Coaxial cable consists of a central conductor, usually copper, surrounded by an insulating layer, a metallic shield, and an outer insulating layer. The metallic shield helps protect the signal from external interference.
There are two types of coaxial cables: thicknet and thinnet.
Thicknet (10BASE5): Thicker coaxial cable with a greater transmission distance. It can carry signals up to 500 meters. It offers a speed of 10 megabits per second. It uses baseband trasmission. Because of these properties, in ethernet standards, it is specified as the 10Base5 (10 megabits per second Baseband transmission over 5 hundred meters) cable. In a network, it is used as the backbone cable. It connects different network segments.
Thinnet (10BASE2): Thin and flexible coaxial cable, commonly used in older Ethernet networks. It can carry signals up to 200 meters. It offers a speed of 10 megabits per second. It also uses baseband transmission. In ethernet standards, it is specified as the 10Base5 (10 megabits per second Baseband transmission over 2 hundred meters) cable. In a network, it connects end devices such as PCs and printers to the network segment.
Advantages:
- Higher bandwidth compared to twisted pair.
- Better resistance to electromagnetic interference.
- Suitable for longer distances than twisted pair.
Disadvantages:
- More expensive and less flexible than twisted pair.
- Susceptible to signal attenuation over long distances.
- Single point of failure if the cable is damaged.
Fiber Optics:
Fiber optic cables use light signals to transmit data. They consist of a core made of glass or plastic fibers surrounded by a cladding layer that reflects light back into the core. The outer layer is a protective jacket.
Instead of copper Fiber optic cable use glass to carry signals. Since it uses glass to transport signals, electromagnetic interference (EMI) does not affect it.
It reflects light from one endpoint to another. Based on how many beams of light are transmitted at a given time, there are two types of fiber optical cable: SMF (Single-mode fiber) and MMF(multi-mode fiber).
Single-mode fiber (SMF): SMF carries only a single beam of light. It uses a laser as the light source and transmits 1300 or 1550 nano-meter wavelengths of light. It is more reliable and supports much higher bandwidth and longer distances than the MMF cable.
Multi-mode fiber (MMF): MMF carries multiple beams of light. Since it uses multiple beams, it can carry more data than the SMF cable. It uses an LED as the light source and transmits 850 or 1300 nano-meter wavelengths of light. It is used for shorter distances.
Advantages:
- High bandwidth and data transmission rates.
- Immune to electromagnetic interference.
- Low signal attenuation over long distances.
- Lightweight and thin, making it suitable for high-density installations.
Disadvantages:
- More expensive to install compared to copper cables.
- Sensitive to bending and stretching.
- Requires specialized equipment for termination and maintenance.
Wireless Networks:
“Wireless” means without wire. The term wireless network stands for the network where the connections are made without the physical wired connection. Wireless networks do not use any form of cable. It uses radio waves or infrared signals to transmit data between devices without the need for physical cables.

Advantages:
- Mobility: Wireless networks provide greater mobility, allowing devices to connect without being physically tethered to a fixed location.
- Convenience: Users can access the network from various locations within the signal range without the constraints of cables.
- Scalability: It is easier to add new devices to a wireless network, making it more scalable for expanding network requirements.
Disadvantages:
- Interference: Wireless networks can be susceptible to interference from other electronic devices or obstacles such as walls and buildings.
- Security: Wireless networks may be more vulnerable to unauthorized access if not properly secured.
- Speed: While wireless technologies have improved, wired networks often offer faster and more consistent data transfer rates.
Common Technologies:
- Wi-Fi is the most common technology for wireless networks in homes, offices, and public spaces.
- Bluetooth is another wireless technology primarily used for short-range connections between devices.
Difference between Wired Network and Wireless Network:
| Wired Network | Wireless network |
| Wired networks use physical cables or wires to connect devices. | Wireless networks do not use any form of cable. |
| In wired network data travels via cable. | In wireless network data travels over a radio wave or infrared signals. |
| Require more effort and time for installation due to the need to lay cables. | Are quicker to set up since they don’t involve physical cables. |
| Wired networks are considered more secure than wireless as data travels through physical cables. | Less secure than wired network |
| Devices in a wired network have limited mobility. | Offer greater mobility since devices can connect to the network without being physically attached. |
| Wired networks often provide higher data transfer rates. | Usually slower than wired network. |
| Wired networks are generally more stable and reliable. | Reliability and stability of wireless networks are prone to interference by other networks, wireless enabled devices, and objects such as walls that can obstruct the connection |
| Higher initial installation costs due to the need for cables, connectors, and additional infrastructure. | Lower initial installation costs, but ongoing maintenance and periodic upgrades may be required. |
| Experience minimal interference since data travels through shielded cables. | Can be susceptible to interference from other electronic devices, physical obstacles, and environmental factors, potentially affecting signal quality and reliability. |
Broadcast and Point to Point Networks:
Transmission media is basically divided into two categories: Broadcast Networks, Point-to-Point Networks.
Broadcast Network:
Broadcast networks transmit data to all devices on the network. In a broadcast network, all devices on the network share a common communication channel or medium. When one device sends a message, all other devices on the network receive it.
Characteristics:
- Single Channel: All devices use the same communication channel to transmit and receive data.
- Shared Medium: Devices share the communication medium, which can be a cable or a wireless channel.
- Broadcast Address: Messages are usually sent to a broadcast address, allowing all devices to receive and process the message.
- Efficiency: Broadcasting is efficient for one-to-many or many-to-many communication scenarios.
Examples:
- Ethernet networks in their traditional form are broadcast networks, where data is sent to all devices on the network.
- Wireless LANs (Local Area Networks) also utilize a broadcast mechanism.
Point-to-Point Network:
Point-to-point networks involve direct communication between two devices. In a point-to-point network, each communication link connects exactly two devices, forming a dedicated communication path between them.
Characteristics:
- Direct Connection: Each device is directly connected to one other device.
- Dedicated Path: The communication path between two devices is dedicated and not shared with other devices.
- Efficiency: Point-to-point connections can be more efficient for one-to-one communication but may require more resources to establish and maintain.
Examples:
- Traditional telephone networks use point-to-point connections between individual phones.
- Wide Area Networks (WANs) often use point-to-point links for dedicated connections between remote locations.
Network Topologies:
Network topology refers to the physical or logical layout of interconnected devices (nodes) in a computer network. It defines how these devices are connected and how they communicate. Topology refers to the shape of a network or the network’s layout. How different nodes in a network are connected to each other and how they communicate is determined by the network’s topology.
A topology can be described by the way the workstations are physically connected to the network, or by the way the data appear to flow through the network. Different topologies have varying advantages and disadvantages in terms of performance, scalability, and fault tolerance.
There are two types of topologies: Physical and Logical
Physical Topology: The physical topology of a network refers to the configuration of cables, computers and other peripherals.
Logical Topology: A physical topology describes the network, whereas the logical topology describes the network from the viewpoint of the data travelling on the network. Networks can have different physical and logical topologies.
Here are some common Network Topologies:
Bus Topology:
A physical bus topology connects all networked devices to a single continuous cable with a terminator at each end. All devices on the network share a common communication channel, which is a single cable, often referred to as the “bus” or the “backbone”. This cable runs throughout the network, connecting all devices. Data is transmitted along the bus, and each device receives the data, but only the intended recipient processes it. In a logical bus topology, all network communications are broadcast to the entire network.

Key characteristics of Bus Topology:
Single Continuous Cable: All devices on the network share a common communication channel, which is a single cable. This cable runs throughout the network, connecting all devices.
Terminators at Each End: The bus topology requires terminators at both ends of the cable. These terminators help absorb signals and prevent them from bouncing back and causing interference on the network.
Shared Medium: Since all devices use the same cable to transmit and receive data, it is a shared medium. This means that only one device can transmit at a time, and all other devices on the bus can hear the transmission.
Collisions: Collisions can occur if two devices attempt to transmit data simultaneously. To manage collisions, bus networks often use protocols such as Carrier Sense Multiple Access with Collision Detection (CSMA/CD).
Advantages:
- Easy to connect a computer or peripheral to a linear bus.
- Requires less cable length than a star topology
- Simple and cost-effective for small networks.
- Devices can be easily added or removed from the bus without affecting the overall network.
- Troubleshooting in bus topology is often simpler compared to other topologies.
Disadvantages:
- The entire network is dependent on a single communication channel (the bus). If the central cable fails or is damaged, the entire network shuts down
- The length of the bus and the number of devices that can be connected are limited.
- Terminators are required at both ends of the backbone cable.
- Difficult to identify the problem if the entire network shuts down.
- Heavy network traffic significantly slows the network.
- As the number of devices increases or when there is heavy network traffic, collisions may occur.
Star Topology:
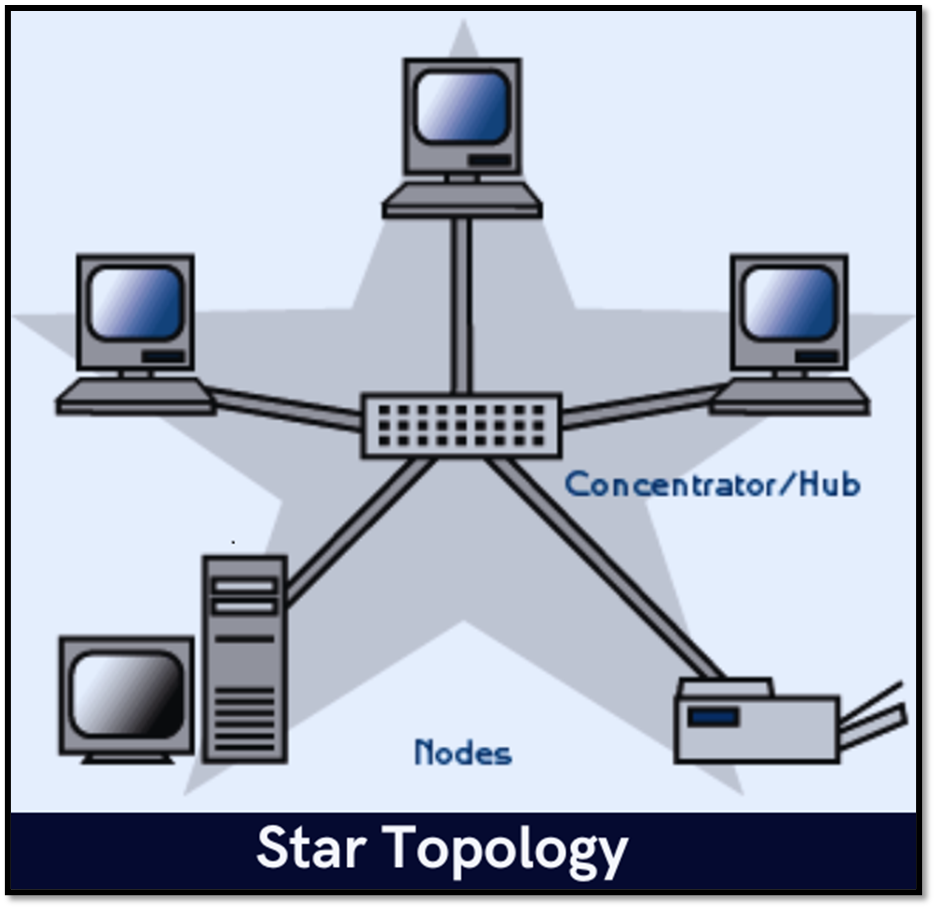
A star topology is designed with each node connected directly to a central hub or switch. The hub manages communication between devices. Data on a star topology passes through the hub or switch before continuing to its destination. The hub or switch manages and controls all functions of the network.
A physical star topology is one in which all branches of the network are connected through a hub. A logical star topology is one in which the hub contains all of the intelligence of the network and directs all network transmissions.
Key characteristics of a Star Topology:
Central Hub or Switch: The central device (hub or switch) serves as a central point of connection for all the nodes in the network. Nodes do not directly connect to each other; instead, they connect to the central hub or switch.
Point-to-Point Connections: Each node has a dedicated connection to the central hub or switch. This results in a point-to-point connection between the node and the central device.
Isolation of Nodes: Unlike bus or ring topologies, the failure of one node in a star topology does not affect the rest of the network. Each node operates independently of the others, and communication between nodes occurs through the central hub or switch.
Scalability: It’s relatively easy to add or remove nodes in a star topology without affecting the overall network. This makes the star topology scalable and flexible.
Reliability: If one node or cable fails, it doesn’t impact the connectivity of other nodes in the network. The failure is isolated to the affected node or cable.
Ease of Management: The central hub or switch simplifies network management. Monitoring and troubleshooting can be more straightforward as all connections are centralized.
Advantages:
- Setting up a star topology is relatively easy.
- Easy to manage and maintain the network because each node requires separate cable.
- Easy to locate problems because cable failure only affects a single user.
- Easy to extend the network without disturbing to the entire network.
- Fault identification and removing nodes in a network is easy.
- It provides very high speed of data.
- Star topology can provide high performance, especially when compared to bus topology.
Disadvantages:
- The entire network’s functionality depends on the central hub or switch. If the hub fails, the entire network is affected
- Establishing a central hub with the necessary switching equipment can be costly, especially in larger networks.
- In larger star topologies, the cabling structure can become complex. Managing and organizing a large number of cables connected to the central hub can be challenging.
- While star topology is generally scalable, there may be limitations based on the capacity of the central hub or switch. As the number of devices increases, the central equipment may reach its maximum capacity, requiring an upgrade or replacement.
Ring Topology:
The ring topology is a physical, closed loop consisting of point-to-point links. All devices are connected in a circular fashion, forming a closed loop, so that each device is connected directly to two other devices, one on either side of it.
A physical ring topology is a network configuration in which each device or node is connected to exactly two other devices, forming a closed loop or ring. Unlike other topologies, such as star or bus, where devices are connected to a central point or a shared communication line, a physical ring topology involves a circular pathway for data transmission. Data travels in one direction around the ring. In a logical ring, data flow from one node to the next in an ordered sequence. When the data reach the last node, they are returned to the origin node.

Key characteristics of Ring Topology:
Circular Pathway: Each device is connected to exactly two other devices, forming a continuous loop or ring. The last device in the ring is connected to the first one, creating a closed circuit.
Unidirectional or Bidirectional Communication: Data can travel in either a unidirectional or bidirectional manner around the ring. In a unidirectional ring, data travels in one direction only, while in a bidirectional ring, data can circulate in both directions.
Reliability: Ring topologies are known for their reliability. If one link or device in the ring fails, the data can still travel in the opposite direction, ensuring that the network remains operational. However, if there is a failure at two points simultaneously, the network may become disrupted.
Simple Structure: The physical structure of a ring topology is relatively simple, making it easy to install and configure.
Token Passing: In ring networks, a token-passing protocol is often used to control access to the network. Only the device with the token has the right to transmit data, which helps avoid collisions.
Advantages:
- Simple and easy to set up, no central device.
- Unlike star topology, ring topology doesn’t depend on a central hub or switch. If one device fails, it doesn’t necessarily disrupt the entire network.
- In smaller networks with a limited number of devices, ring topology can be cost-effective. The simplicity of the design and the absence of a central hub can result in lower initial setup costs.
- Ring topology generally requires less cabling compared to mesh topology, where every device is connected to every other device. This can reduce the overall cost of the network infrastructure.
- Ring topology is well-suited for applications where data needs to be transmitted sequentially from one device to the next.
Disadvantages:
- If any device or connection in the ring fails, the entire network can be disrupted. This makes ring topology less fault-tolerant compared to other topologies.
- Ring topology is not easily scalable. Adding or removing devices can disrupt the entire network, as it requires breaking the ring and reconfiguring connections Ring topology can pose security concerns as data circulates through the entire network.
- Ring topology becomes less practical as the size of the network increases. In a ring topology, data travels in both directions along the ring. If multiple devices attempt to transmit data simultaneously, collisions can occur, leading to data corruption and decreased network performance.
- The bandwidth in a ring topology is shared among all devices in the network. As more devices are added to the ring, the available bandwidth for each device decreases. This can result in slower data transfer rates, especially during periods of high network traffic.
Mesh Topology:
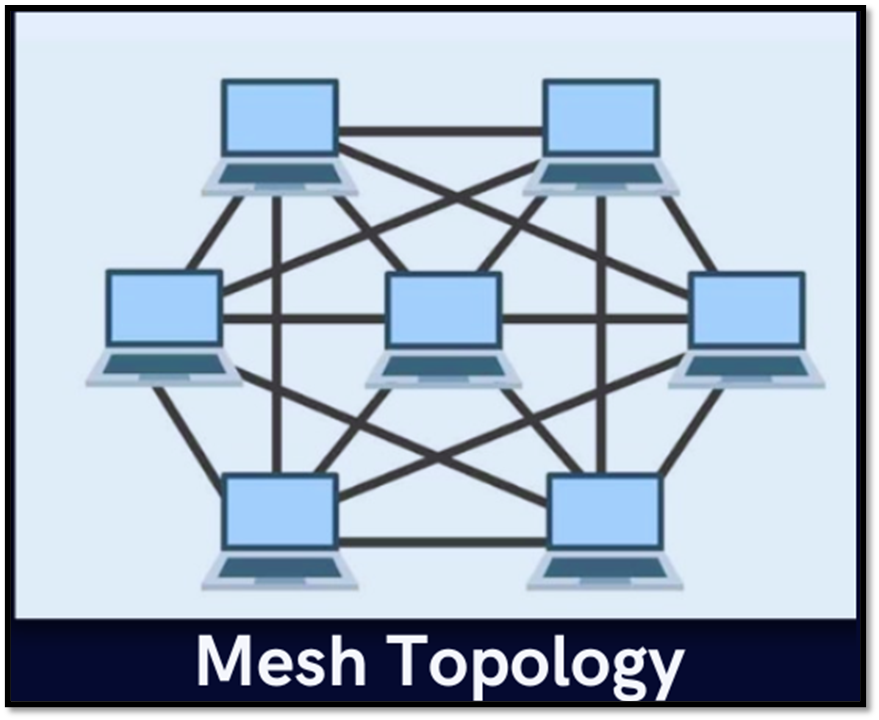
Mesh topology is a network configuration where every node is connected to every other node. There are two types of mesh topologies: full mesh (direct connections between all devices) and partial mesh (some devices have direct connections to every other device).
Key characteristics of Mesh Topology:
Reliability and Redundancy: Mesh topologies provide high reliability and redundancy due to the multiple paths for communication. If one link or node fails, alternative paths can be used.
Scalability: Mesh topologies can be scalable, but the number of connections increases rapidly with each new device, making it challenging to manage in large networks.
Complexity and Cost: Full mesh topologies, in particular, can be complex to implement and expensive due to the large number of required connections. Partial mesh topologies offer a balance between complexity and redundancy.
Used in Critical Applications: Mesh topologies are often used in critical applications where reliability and fault tolerance are essential, such as in telecommunications networks or mission-critical systems.
Advantages:
- One of the significant advantages of mesh topology is its high level of fault tolerance. If one link or node fails, communication can continue through alternative paths.
- In a mesh topology, data can be sent directly between nodes without passing through a central point. This can enhance privacy.
- Due to the multiple paths available for communication, mesh topology can reduce latency.
- There is no traffic problem as there are dedicated point to point links for each node.
- Due to the multiple paths for communication, mesh topology provides high reliability. If one link or node experiences issues, data can be rerouted through other available paths, minimizing the chances of network downtime.
Disadvantages:
- One of the primary disadvantages of mesh topology is the high cost associated with its implementation. The sheer number of cables and network interfaces required for a fully meshed network can be expensive to install and maintain.
- Mesh networks tend to be complex in terms of design and maintenance. As the number of nodes increases, the complexity of managing and troubleshooting the connections also grows, requiring more time and resources.
- Identifying and resolving faults in a mesh network can be more difficult compared to simpler topologies.
- Setting up a mesh network with numerous point-to-point connections can be time-consuming. Each device needs to be individually connected to every other device, and this process can be lengthy, particularly in large-scale networks.
- Expanding a mesh network can be challenging. As the number of nodes increases, the number of connections grows exponentially, making it difficult to scale the network.
Tree Topology:
Tree topology is a type of network topology that combines characteristics of both bus and star topologies. It is called a “tree” because it resembles an inverted tree structure, with a main root node or hub and branches connecting to various nodes in a hierarchical fashion.

Key characteristics of a Tree Topology:
Hierarchical Structure:
- The network is organized in a hierarchical manner, with a central root node or hub at the top.
- The root node is connected to secondary nodes, forming levels or layers of the hierarchy.
- Each secondary node can act as a sub-hub, branching out to additional nodes.
Central Hub or Root Node:
- The central hub (root node) is a critical component in the tree topology.
- All communication passes through the central hub, which helps in managing and controlling the network.
Point-to-Point Connections:
- Nodes are connected to the central hub using point-to-point connections, such as cables or wireless links.
- Each node in the network has a unique connection path to the central hub.
Scalability:
- Tree topology is easily scalable by adding branches or levels to accommodate new nodes.
- The hierarchical structure allows for the expansion of the network without affecting the entire topology.
Reliability:
- Tree topology provides a level of redundancy. If a connection fails in one branch, it doesn’t necessarily affect the entire network.
- The hierarchical structure contributes to better fault isolation and easier troubleshooting.
Flexibility:
- It offers flexibility in terms of adding or removing nodes without disrupting the entire network.
- Changes can be made at the leaf nodes without affecting other parts of the topology.
Complexity and Cost:
- Tree topology can be more complex and costly to set up compared to simpler topologies like bus or star.
- The central hub requires more sophisticated equipment, and the cabling structure can be extensive.
Performance:
- Performance may be affected if the central hub becomes a bottleneck, especially in networks with heavy traffic.
- However, the hierarchical structure can help manage and control traffic flow efficiently.
Advantages:
- It can support a large number of nodes.
- Tree topology is easily scalable. As the network expands, additional branches or levels can be added without affecting the overall structure.
- Tree topology reduces traffic on the network. The hierarchical structure of the network allows for the distribution of traffic.
- Tree topology can offer better performance compared to linear topologies like bus or ring.
- Devices in the other hierarchies of the network are not harmed if any of the devices in one of the branches of the network is damaged.
Disadvantages:
- Tree topology typically has a central hub or switch at its core. If this central device fails, it can disrupt the entire network.
- More difficult to configure and wire than other topologies.
- The performance of the entire network can be affected by the central hub’s capacity. If the hub becomes overloaded due to high traffic or a large number of connected devices, it can create performance bottlenecks.
- Troubleshooting and maintaining a tree topology network can be challenging. Identifying and resolving issues, especially in larger networks, may require skilled personnel and efficient management tools.
- Tree topology can become complex as the network grows. Managing multiple branches and connections requires careful planning and organization, and the complexity increases with the addition of more devices and branches.
Hybrid Topology:
A hybrid topology is a network configuration that combines two or more different types of topologies into one overall structure. The hybrid topology combines two or more different types of topologies into one large topology. Hybrid topology is common in large wide-area networks. Because each topology has its own strengths and weaknesses, several different types can be combined for maximum effectiveness.

Key characteristics of Hybrid Topology:
Use of Multiple Topologies: Hybrid topologies use a combination of two or more basic topologies like star, bus, ring, or mesh.
Integration of Topologies: Different parts of the network may be organized using different topologies, and these parts are interconnected to form a larger, cohesive network.
Customization and Optimization: Hybrid topologies are designed to take advantage of the strengths of each topology used. For example, a star-bus hybrid might combine the scalability of a bus with the reliability and ease of management of a star.
Scalability and Flexibility: Hybrid topologies offer scalability and flexibility, allowing for customization to meet specific requirements in different sections of the network.
Fault Tolerance: By combining different topologies, hybrid networks can provide increased fault tolerance. If one part of the network fails, other parts may remain operational.
Application-Specific Design: Hybrid topologies are often employed in large networks, data centers, or in situations where different areas of the network have different requirements.
Advantages:
- Hybrid topology combines the benefits of different types of topologies.
- Hybrid topologies offer flexibility in designing the network based on specific requirements.
- Hybrid topology is scalable. Easy to increase the size of network by adding new components without disturbing existing architecture.
- Hybrid topology is reliable. By combining different topologies, the overall network becomes more resilient.
- In hybrid topology fault detection is easy. The part in which fault is detected can be isolated from the rest of network and required corrective measures can be taken.
Disadvantages:
- Hybrid topologies can be more complex to design, implement, and manage compared to simpler topologies.
- Implementing a hybrid topology can be expensive. It may involve the purchase of various networking equipment and infrastructure to support different topologies.
- Network administrators and support staff may require additional training to handle the complexity of a hybrid topology.
- Integrating different topologies may introduce security vulnerabilities.
- Some hybrid topologies may rely on central components like a main server or hub. If this central component fails, it can disrupt the entire network.
Network Protocols:
Network protocols are a set of rules that governs data communications. Protocols governs how data is exchanges and transmitted between devices on a computer networks. It represents an agreement between the communication devices. Without a protocol, two devices may be connected but not communicating. These protocols ensure that devices on a network can communicate with each other effectively.
The rules that allow computers to communicate in a network are called protocols. Protocols are sets of rules for message formats and procedures that allow machines and application programs to exchange information. These rules must be followed by each machine involved in the communication in order for the receiving host to be able to understand the message.
The main protocol for transferring information on the web is the Hypertext Transfer Protocol (HTTP). Web pages, both text and graphics are sent from the server to the browser using this protocol.
The web also supports most of the other popular internet protocols, such as TCP/IP, FTP, PPP, SLIP etc. We need not remember all these protocols. The browser does all the work, dynamically switching between protocols as needed.
Here are some key Network Protocols:
TCP/IP (Transmission Control Protocol/Internet Protocol): This is a suite of protocols that includes several individual protocols, such as:
- TCP (Transmission Control Protocol): Provides reliable, connection-oriented communication between devices in a network.
- IP (Internet Protocol): Manages the addressing and routing of data packets across networks.
- UDP (User Datagram Protocol): Provides a connectionless and faster protocol for communication, suitable for applications where some packet loss is acceptable.
HTTP (Hypertext Transfer Protocol): The foundation of data communication on the World Wide Web. It is used for transmitting hypertext (web pages) between a web server and a web browser.
HTTPS (Hypertext Transfer Protocol Secure): A secure version of HTTP, encrypting data during transmission.
FTP (File Transfer Protocol): Used for transferring files between computers on a computer network.
SMTP (Simple Mail Transfer Protocol): It is a protocol used in computer networks to send emails from a client to a server or between servers. It is specifically designed for the transmission of email messages.
POP3 (Post Office Protocol version 3): A protocol used for retrieving email from a server.
IMAP (Internet Message Access Protocol): Another email retrieval protocol, which is more advanced than POP3 and allows for managing emails on the server.
DNS (Domain Name System): Translates human-readable domain names into IP addresses, making it easier for users to remember and use domain names instead of numeric IP addresses.
DHCP (Dynamic Host Configuration Protocol): Assigns IP addresses dynamically to devices on a network, eliminating the need for manual configuration.
SNMP (Simple Network Management Protocol): Used for managing and monitoring network devices and their functions.
ISO/OSI Reference Model:
The OSI (Open Systems Interconnection) model, developed by the International Organization for Standardization (ISO), serves as a blueprint for understanding how data moves from one device to another in a network.
Open System Interconnection is a conceptual model that describes how data moves from one computer to another over a network. It is a layered model consisting of seven layers, each layer providing a specific functionality to enable communication between computers. The OSI model provides a systematic approach to understanding and designing communication systems. It helps ensure that different systems can communicate with each other and the communication is reliable.
The OSI (Open System Interconnection) model is a conceptual framework used to describe the functions of a communication system. It consists of seven layers, each with a specific set of responsibilities.
The seven layers of the OSI model are:
1. Physical Layer:
This is the lowest layer of the OSI model and deals with the physical transmission of data over the network medium. The physical layer is responsible for transmitting and receiving raw bit streams over a communication channel. This layer defines the electrical, mechanical, and physical characteristics of the communication medium, such as cables, connections and wireless frequencies.
The main function of the physical layer is to move data in the form of electromagnetic signals across a transmission medium.
Functions of Physical layer:
Line Configuration: It defines how two or more devices can be connected physically
Data transmission: Defines whether the transmission is simplex, half duplex or full duplex.
Topology: It defines the way how network devices are arranged.
Signals: Determines the type of signals used for transmitting information.
2. Data Link Layer:
The data link layer is responsible for the node-to-node delivery of data over a physical network. Its main function is to provide a reliable and error free transmission of data between two devices in the network. When a packet arrives at the DLL, it is responsible for ensuring that the packet is delivered to the correct device on the network.
This layer is responsible for framing, error detection and correction of data and it also manages the flow of data between devices.
Functions of the DLL:
1. Framing: The DLL takes the packets from the network layer and encapsulates them into frames. It sends each frame bit by bit on the hardware.
Header: It contains the source and the destination addresses of the frame.
Trailer: It contains the error detection and error correction bits.
Physical addressing: The DLL adds a unique Media Access Control (MAC) address to each frame, which identifies the source and destination devices on the network. The MAC address is used by the network hardware to deliver the frame to the correct destination.
Flow control: It is a speed matching mechanism. Flow control coordinates the amount of data that can be sent before receiving an acknowledgement. It prevents data loss and buffer overflow.
Access Control: Provides a mechanism for multiple devices to access the shared physical medium without causing data collisions.
Error Control: Detecting and correcting errors that may occur during transmission., using techniques such as cyclic redundancy check (CRC) and acknowledgement.
3. Network Layer:
The network layer is responsible for the delivery of data between nodes on different networks. It provides routing and address services to move data from the source to the destination network.
The network layer works for the transmission of data from one host to the other located in different networks. It also takes care of packet routing i.e., selection of the shortest path to transmit the packet , from the number of routes available. The sender and receiver’s IP address are placed in the header by the network layer.
This layer defines the addressing scheme and the protocols used to route data between networks. The IP (Internet Protocols) is an example of a protocol used at this layer.
Functions:
Routing: The network layer protocols determines which route is suitable from source to destination. This function is known as routing.
Logical Addressing: To identify each device on the internet uniquely, the network layer defines an addressing scheme. The sender and receiver’s IP addresses are placed in the header by the network layer.
4. Transport Layer:
The transport layer is responsible for end-to-end communication between the sender and receiver. It ensures that data is delivered reliably and in the correct order through mechanisms like segmentation, flow control, and error correction. Transmission Control Protocol (TCP) and User Datagram Protocol (UDP) are the two main protocols at this layer.
Functions of Transport Layer:
Segmentation and reassembly: divide data into smaller segment for efficient transmission.
Connection Management: establish, maintain and terminate connections between applications.
Reliable data delivery: ensure error-free transmission through error detection and correction.
Flow control:
Congestion control:
5. Session Layer :
The session layer establishes, manages, and terminates connections between applications. It allows multiple applications to communicate over the network simultaneously and provides services like session establishment, maintenance, and synchronization.
Functions of Session Layer:
Synchronization: session layer adds some checkpoints when transmitting the data in a sequence. If some error occurs in the middle of the transmission of data, then the transmission will take place again from the checkpoint.
Dialog control: regulates the flow of data between applications to ensure orderly communication.
6. Presentation Layer
The presentation layer is responsible for data translation, compression, encryption, and decryption. It translates the data from the application layer into a standardized format that can be understood by different systems. It also provides encryption and decryption services to protect data during transmission.
The presentation layer is mainly concerned with the syntax and semantics of the information exchanged between two systems. It acts as a data translator for a network. It ensures that data sent by the application layer is properly formatted and readable by the receiving application.
Functions of Presentation Layer:
Data translations: It translates data between different character sets such as ASCII and Unicode.
Data formatting and syntax checking: it ensures that data is formatted properly and follows the correct syntax.
Data encryption and decryption : it encrypts data to ensure secure transmission, and decrypts it at the receiving end.
Data compression: it reduces the number of bits to be transmitted
7. Application Layer :
The application layer is the closest layer to the end-user and provides network services directly to user applications. The application layer is responsible for providing services to end users. It is responsible for providing user interface and communication service that enables the applications to interact with the network. Application layer defines the protocols and interfaces used by application programs to access the network. Examples include HTTP, FTP, SMTP, and DNS.
Functions of the Applications Layer:
FTAM : File transfer, access and management provides service to transfer files between hosts and to manage the files on remote system.
Mail Service : sending and storing email messages.
Directory services : provides a way for users to locate and access resources on a network.