In written or typed texts, handwritten signatures are frequently used in the physical world. They serve to bind the message’s signatories. A similar method that ties a person or entity to digital data is a digital signature. Digital signatures are a cryptographic tool to sign messages and verify message signatures in order to provide proof of authenticity for digital messages or electronic documents. It is the concept of public-key encryption used for message authentication.
Digital signatures can provide evidence of origin, identity and status of electronic documents, transactions or digital messages. Digital signatures are the most secure way to authenticate the signer’s identity and are strong proof that the signer and no one else has signed the document in question.
A digital signature is a mathematical technique used to validate the authenticity and integrity of a message, software or digital document. It’s the digital equivalent of a handwritten signature or stamped seal, but it offers far more inherent security. A digital signature is a cryptographic value that is calculated based on the data and the secret key of the signer.
Digital signatures are widely used today in the business and in the financial industry, e.g. for authorizing bank payments (money transfer), for exchange of signed electronic documents, for signing transactions in the public blockchain systems (e.g. transfer of coins, tokens or other digital assets), for signing digital contracts and in many other scenarios.
Digital signatures cannot identify who is the person, created a certain signature. This can be solved in combination with a digital certificate, which binds a public key owner with identity (person, organization, web site or other). By design digital signatures bind messages to public keys, not to digital identities.
Digital signature schemes typically use a public key cryptography, also known as asymmetric cryptography (such as RSA or ECC) and use a public / private key pairs. A message is signed by a private key and the signature is verified by the corresponding public key. Messages are signed by the sender using a private key (signing key). Typically the input message is hashedand then the signature is calculated by the signing algorithm. Most signature algorithms perform some calculation with the message hash + the signing key. The produced signed message consists of the original message + the calculated signature.
Message signatures are verified by the corresponding public key (verification key). The signed message is hashedand some computations are performed by the signature algorithm using the message hash + the public key and finally a comparison decides whether the signature is valid or not.
A message signaturemathematically guarantees that certain message was signed by certain (secret) private key, which corresponds to certain (non-secret) public key. After a message is signed, the message and the signature cannot be modifiedand thus message authenticationand integrity is guaranteed. Anyone, who knows the public key of the message signer, can verify the signature. Аfter signing the signature author cannot reject the act of signing (this is known as non-repudiation).
If the recipient can’t open the document with the signer’s public key, that’s a sign there’s a problem with the document or the signature. This is how digital signatures are authenticated.
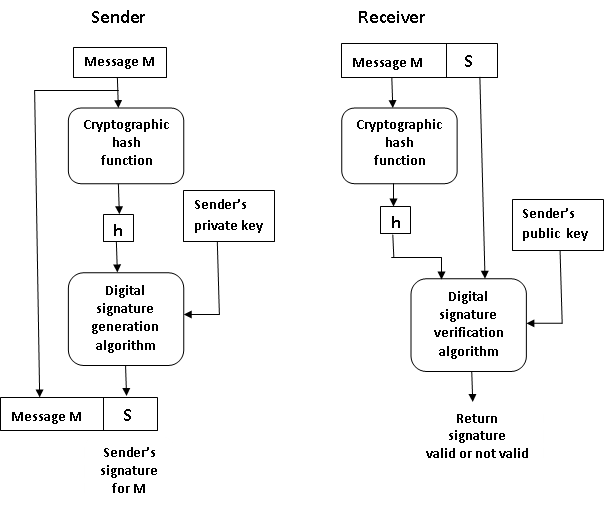
How does Digital Signature Work?
The process involved in the digital signature is as follows:
- The user who adopts has a pair of keys – a public key and a private key. These keys are used for the Encryption and decryption process. The private key is used for the encryption, i.e., signing the signature, or we can say that it is the signature key, and the public key is used for the decryption, i.e. verification key.
- The user, i.e. the signer (sender), apply the cryptographic hash function on the data and creates the hash of data.
- After that, apply a digital signature algorithm on both the hash value and the signature key (private key) to create the given hash’s digital signature.
- Then the signature is appended with data, and both signature and data are sent to the verifier over the network.
- Verifier, i.e. receiver, apply digital signature verification algorithm and verification key (public key). This process gives value as an output.
- Verifier also used the same hash function on the data, which the signer uses to get the hash value.
- Then he verifies the hash value and the output, which is generated by an algorithm. Based on the result, the verifier validates it. If both are the same, the digital signature is valid; otherwise, it is invalid.
(a) Sender signs a message (b) Receiver verifies the signature
Importance of Digital Signature: Why do we need Digital Signature?
Digital signatures have been developed as an application of cryptography and also find extensive utility in network security. The digital signature is one of the best authentication tools for electronic record. On account of its cost, security, time, and speed, digital signatures are popular nowadays. In today’s interconnected and digital world, the digital signature algorithm is vital for creating a safer and secure environment.
Digital signatures are regarded as one of the most crucial and practical cryptographic tool for achieving information security. The digital signature also offers data integrity and message authentication in addition to non-repudiation of the message.
Digital signatures provide:
Message Authentication: A proof that certain known sender (secret key owner) have created and signed the message. It ensures that the message is coming from the intended sender, not other parties. It allows a receiver to verify the digital signature by using the sender’s public key; it ensures that the signature is created only by the sender who uses the secret private key to encrypt the message.
When a sender’s public key is used to authenticate a digital signature, the verifier is confident that the signature has only been created by that sender and no one else.
Data integrity: A proof that the message was not altered after the signing. It provides data integrity to test the modification in the message. If somehow, the attacker gets access to the message and modifies the data. Verification at the receiver side will fail. This is because the hash value of the modified message and the algorithm’s value will not match. In this case, the receiver can reject the message.
The digital signature verification at the receiving end is ineffective if an attacker gains access to the data and alters it. The output of the verification procedure will not match the hash of the updated data. Therefore, presuming that data integrity has been compromised, the receiver can safely reject the message.
Non-repudiation: The signer cannot deny the signing of the document after the signature is once created. As the only sender knows the secret key, i.e. signature key, he is the only one who can create a unique signature on the data. As a result, if a dispute ever occurs, the receiver can show evidence of the data as well as the digital signature to the third party as proof.
Importance of Digital Signature: Why do we need Digital Signature?
One of the best ways to secure information, digital signature has simplified secure communication between individuals, business, market, a government institution.
· A digital signature provides better security in the transaction. Any unauthorized person cannot do fraudulence in transactions.
· You can easily track the status of the documents on which the digital signature is applied.
· High speed up document delivery.
· It is 100% legal it is issued by the government authorized certifying authority.
· If you have signed a document digitally, then you cannot deny it.
· In this signature, when a document is get signed, date and time are automatically stamped on it.
· It is not possible to copy or change the document signed digitally.
· Identification of the person that signs.
· Elimination of the possibility of committing fraud by an imposter.
How are digital signatures created?
A digital signature is created using hash algorithms or a scheme of algorithms like DSA and RSA that use public key and private key encryptions. The sender uses the private key to sign the message digest (not the data), and when they do, it forms a digital thumbprint to send the data.
All the tools used to digitally sign a document are numerical in nature. Digital signature solutions use crypto-algorithms to convert both the document to be signed and the private key (which is already in character form), into a new set of encrypted characters.
When a signed document is authenticated using the public key, the signer is aware of who created it & whether the document has been altered since being digitally signed. The decryption process gets back the original hashed document, and this can be compared to the encrypted hash, to determine the authenticity of the document & the digital signature.
To verify the identity of the signer and the digital signature, DSC or Digital Signature Certificate is issued. DSC is a secure digital public key that does all the decrypting & authenticates the identity of the holder. The underlying process here is far from simple, and it takes multiple algorithms carefully designed to encrypt, decrypt, and authenticate messages & data to create a digital signature.
Here are a few of the most popular algorithms used for digital signatures:
Digital Signature Algorithm (DSA) and RSA
One of the algorithms used to create digital signatures is the Digital Signature Algorithm or DSA, the industry-standard cryptosystem used to create a digital signature.
DSA works based on algebraic properties of discrete logarithmic functions and modular exponentiations to create a digital signature that consists of two 160-bit numbers derived from the message digests and private key.
The other type of algorithm is RSA, named after its inventors – Ronald Rivest, Adi Shamir & Leonard Adleman, who first described it in the late 1970s. RSA is an asymmetric cryptographic algorithm used to encrypt and decrypt messages. Since it uses a public key framework, anyone can have the keys involved in decryption.
In Digital Signature Algorithms, a set of numbers is created, allowing the receiver to authenticate the origin of the message or document. In most cases, the digital signature used in data transmission will be private at the start. Only the person performing the transmission can sign the document, but in the end, anyone can authenticate the signature.
A digital signature is created by pairing the public & private cryptographic keys. DSA by itself, however, can only be used to create a signature and not to encrypt data.
Hashing is another element in creating a digital signature. Hashing is a process of transforming data into a fixed-size output using a hash algorithm called a hash function. The output of the hash function is called a message digest or hash value.
Types of Attacks on Digital Signature:
Following are the three types of attacks that are attempted against the digital signature:
· Chosen Message Attack: The attacker tricks the genuine user into digitally signing a Message that the user does not normally intend to sign. As a result, the attacker gets a pair of the original message that was signed and the digital signature. using this, the attacker tries to create a new message that she wants a genuine user to sign and uses the previous signature.
· Known Message Attack: In this type of attack, the attacker obtains some messages that the user sends and a key to create a new fault message and forge of the user.
· Key only Attack: In this type of attack, it is assumed that the user name some information public and the attacker try to misuse this public information. Attackers try to create the user. RSA and digital signature.
Uses of Digital Signatures:
Industries use digital signature technology to streamline processes and improve document integrity. Industries that use digital signatures include the following:
· Government: Digital signatures are used by governments worldwide for a variety of reasons, including processing tax returns, verifying business-to-government (B2G) transactions, ratifying laws and managing contracts. Most government entities must adhere to strict laws, regulations and standards when using digital signatures. Many governments and corporations also use smart cards to ID their citizens and employees. These are physical cards endowed with a digital signature that can be used to give the cardholder access to an institution’s systems or physical buildings.
· Healthcare: Digital signatures are used in the healthcare industry to improve the efficiency of treatment and administrative processes, to strengthen data security, for e-prescribing and hospital admissions. The use of digital signatures in healthcare must comply with the Health Insurance Portability and Accountability Act (HIPAA) of 1996.
· Manufacturing: Manufacturing companies use digital signatures to speed up processes, including product design, quality assurance (QA), manufacturing enhancements, marketing and sales. The use of digital signatures in manufacturing is governed by the International Organization for Standardization (ISO) and the National Institute of Standards and Technology (NIST) Digital Manufacturing Certificate (DMC).
· Financial services: The U.S. financial sector uses digital signatures for contracts, paperless banking, loan processing, insurance documentation, mortgages and more. This heavily regulated sector uses digital signatures with careful attention to the regulations and guidance put forth by the Electronic Signatures in Global and National Commerce Act (E-Sign Act), state Uniform Electronic Transactions Act (UETA) regulations, the Consumer Financial Protection Bureau (CFPB) and the Federal Financial Institutions Examination Council (FFIEC).
· Cryptocurrencies: Digital signatures are also used in bitcoin and other cryptocurrencies to authenticate the blockchain. They are also used to manage transaction data associated with cryptocurrency and as a way for users to show ownership of currency or their participation in a transaction.
What’s the difference between a digital signature and an electronic signature?
Though the two terms sound similar, digital signatures are different from electronic signatures. Digital signature is a technical term, defining the result of a cryptographic process or mathematical algorithm that can be used to authenticate a sequence of data. The term electronic signature — or e-signature — is a legal term that is defined legislatively.
For example, in the United States, the E-Sign Act, passed in 2000, defined e-signature as meaning “an electronic sound, symbol or process, attached to or logically associated with a contract or other record and executed or adopted by a person with the intent to sign the record.”
E-signatures are also defined in the Electronic Signatures Directive, which the European Union (EU) passed in 1999 and repealed in 2016. It regarded them as equivalent to physical signatures. This act was replaced with eIDAS (electronic identification authentication and trust services), which regulates e-signatures and transactions, and the embedding processes that ensure the safe conduct of online business.
This means that a digital signature — which can be expressed digitally in electronic form and associated with the representation of a record — can be a type of e-signature. More generally, though, an e-signature can be as simple as the signer’s name being entered on a form on a webpage.
To be considered valid, e-signature schemes must include three things:
1. a way to verify the identity of the entity signing it;
2. a way to verify the signing entity intended to affirm the document being signed; and
3. a way to verify that the e-signature is associated with the signed document.
A digital signature can, on its own, fulfill these requirements to serve as an e-signature:
· the public key of the digital signature is linked to the signing entity’s electronic identification;
· the digital signature can only be affixed by the holder of the public key’s associated private key, which implies the entity intends to use it for the signature; and
· the digital signature will only authenticate if the signed data, i.e., document or representation of a document, is unchanged — if a document is altered after being signed, the digital signature will fail to authenticate.
While authenticated digital signatures provide cryptographic proof a document was signed by the stated entity and the document has not been altered, not all e-signatures provide the same guarantees.