MD5 hashing stands for Message Digest5, introduced by Ronald Rivest. MD5 was developed to replace MD4. It is commonly used to verify data integrity. However, there are several version of MD is created among which the first was the MD (message digest algorithm) followed by MD2, MD3, MD4 and at last MD5. These versions of MD were improving one after the other, the newer version was better than the old one.
The MD5 cryptographic algorithm is not reversible i.e. we cannot decrypt a hash value created by the MD5 to get the input back to its original value. So there is no way to decrypt an MD5 password. But, we can use something like brute force hacking, which is extremely resource-intensive, not practical, and unethical.
The MD5 hash function was originally designed for use as a secure cryptographic hash algorithm for authenticating digital signatures.
MD5 (Message Digest Method 5) is a cryptographic hash algorithm used to generate a 128-bit digest from a string of any length. The digest size is always 128 bits. A minor change in the input string generates a drastically different digest. This is essential to prevent similar hash generation as much as possible, also known as a hash collision.
MD5 algorithm takes an input with any length and it generates an output with 128 bit length which is named as finger-print or message digest. MD5 algorithm was designed for digital signing applications. MD5 algorithm was designed to run fast in 32 bit computers for long files.
MD5 was the fastest algorithm produced in that era and was able to protect itself from collisions. At present, it may not assure its security as the hacker and technology discovered the way to create collisions. It creates 128-bit messages where input text is processed in 512-bit blocks which are further separated into 16 32-bit sub-blocks. The result of the MD5 algorithm built a set of four 32-bit blocks which creates a 128-bit message digest.
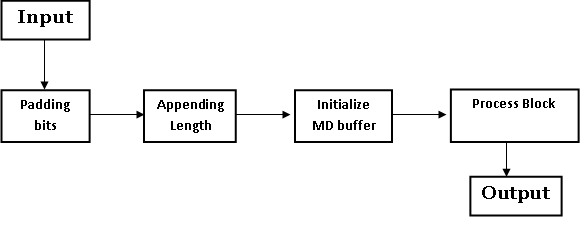
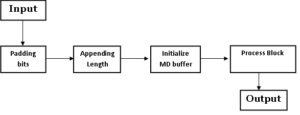
MD5 Working:
Steps in MD5 Algorithm:
There are four major sections of the algorithm:
Padding Bits:
When you receive the input string, you have to make sure the size is 64 bits short of a multiple of 512. You’ll extend the total length of the original input so it’s 64 bits short of any multiple of 512. When it comes to padding the bits, you must add one (1) first, followed by zeroes to round out the extra characters.
Appending Length:
A 64-bit representation of length of message before padding bits were added is appended to the result of the previous step.
You need to add a few more characters to make your final string a multiple of 512. To do so, take the length of the initial input and express it in the form of 64 bits. On combining the two, the final string is ready to be hashed. With this operation, the total number of bits in the message becomes a multiple of 512 (i.e., 64 bits).
Initialize MD Buffer:
The entire string is converted into multiple blocks of 512 bits each. You also need to initialize four different buffers, namely A, B, C, and D. These buffers are 32 bits each and are initialized as follows:
A = 01 23 45 67
B = 89 ab cd ef
C = fe dc ba 98
D = 76 54 32 10
Process Block:
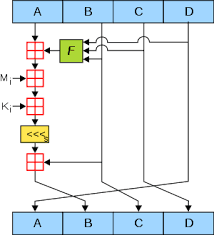
In this step, the actual algorithm starts working. Each 512-bit block gets broken down further into 16 sub-blocks of 32 bits each. There are four rounds of operations, with each round utilizing all the sub-blocks, the buffers, and a constant array value. Each block is processed using four rounds of 16 operations and adding each output to form the new buffer value.
A single round is explained in the diagram given below:
Each round is consist of 16 input sub-blocks named as M[0], M[1],…., M[15] or commonly, M[i], where i ranges from 0-15. Additionally, there is an array of constants are given as input denoted by K, K[1], K[2],…, K[64] or in general as K[i] where k varies from 1 to 64 but only 16 are used out of the 64 values of K.
In summary, the original input is broken up into fixed-sized blocks, then each one is processed through the compression function alongside the output of the prior round. The final output is a 128 bits message digest.